One I have been looking at is in regards to optimising VDI for the WAN, with acceleration via Cisco WAAS.
When you look at the excellent Cisco Application Networking Services for VMware Virtual Desktop Infrastructure Deployment Guide, which I highly recommend, you start to see a few security issues opening up.
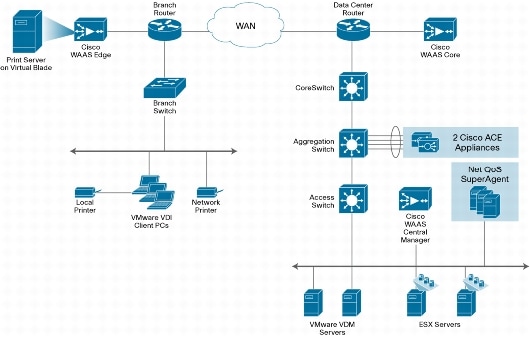
In summary to get good acceleration over the WAN you need to remove the compression and disable the encryption of the RDP traffic. This allows the WAN accelerator visibility of the contents in order to perform its own acceleration. By following this best practice you open up a new security risk.
People type a lot of information into their desktops and they may not be happy that its not as secure as they they think it is. When your user is using their Internet banking at the office they expect that what they are typing into that VDI desktop is 100% secure from everyone in the organisation.
Of course encryption can be put back in place, between the WAN acceleration devices. However one is going to need to consider the load and scaling issues associated with this. Its nice when this encryption load is distributed across the VDI guest machines and the thin clients rather than consolidated down to a few boxes. What about the traffic between the ESX hosts and the accelerators, will a separate vLAN suffice?
Another consideration is what to do when you have a mixed environment. What if only a portion of your users in your pool are going over the WAN, how do you control and manage which guests get it turned off.
I am sure that there are some good solutions that can be designed into an implementation to mitigate these risks. We just need to raise awareness so people know that it needs to be addressed.
If anyone has done any work on this join the discussion. Maybe this is something for the VMware Communities Roundtable or the Virtualization Security Roundtable?
Rodos
No comments:
Post a Comment